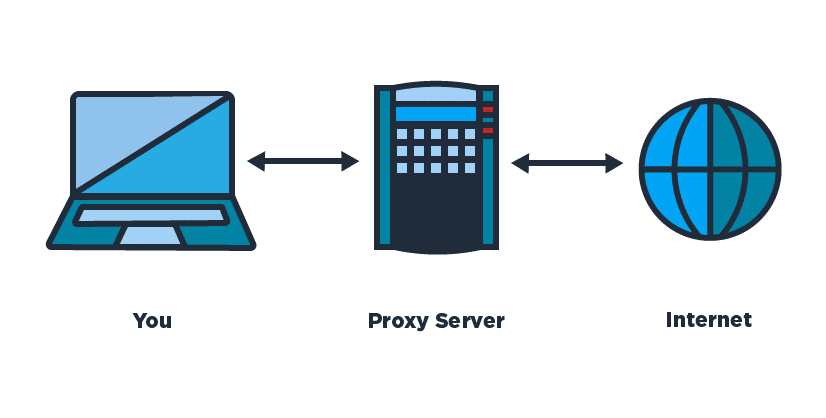
Data security isn’t a luxury; it’s a necessity, especially in environments as sensitive as virtual data rooms (VDRs). These spaces, often used during mergers, acquisitions, or other high-stakes transactions, house a treasure trove of confidential information. But with great value comes great risk, particularly in the form of cyber threats targeting data transmission. Here, proxies […]